Purpose : To Configure Single sign on for Oracle fusion middleware products like SOA, UCM, Web Center spaces etc.
This method of enabling SSO using the Microsoft active directory - Key Distribution center has the following configuration steps. Suggest a detailed analysis of every step marked below before executing them on to your servers.
c. Weblogic Server 10.3.5.0
OS: Oracle Enterprise Linux 5 64 bit.
Machine: node1 and node2
Active Directory Setup.
Create an user in Active Directory with below details.
User Name : kerberosadm(Name this user anything that suits your situation)
Pw : Password1 ( An example to reiterate the same password is referenced in later sections during password reset)
The user account’s encryption type must be DES and the account must require Kerberos pre-authentication.
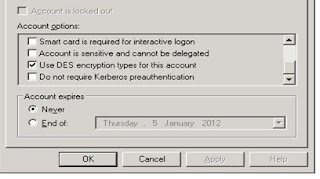
Please do not select any other option than to keep the option "use DES encryption types for this account" checked.
Node1 :
ktpass -princ HTTP/node1.domain.com.au@DOMAINABC.COM -pass Password1 -mapuser kerberosadm -pType KRB5_NT_PRINCIPAL -crypto DES-CBC-CRC -kvno 0 -out node1.HTTP.keytab
Node2:
ktpass -princ HTTP/node2.domain.com.au@DOMAINABC.COM -pass Password1 -mapuser kerberosadm -pType KRB5_NT_PRINCIPAL -crypto DES-CBC-CRC -kvno 0 -out node2.HTTP.keytab
URL:
ktpass -princ HTTP/fusiontest.domain.com.au@DOMAINABC.COM -pass Password1 -mapuser kerberosadm -pType KRB5_NT_PRINCIPAL -crypto DES-CBC-CRC -kvno 0 -out fusiontest.HTTP.keytab
AD User:
ktpass -princ HTTP/kerberosadm.domain.com.au@DOMAINABC.COM -pass Password1 -mapuser kerberosadm -pType KRB5_NT_PRINCIPAL -crypto DES-CBC-CRC -kvno 0 -out kerberosadm.HTTP.keytab
Note: Here I'm configuring SSO for 2 node weblogic cluster and F5 load balancer. So the steps may slightly alter depending on your configuration.
Create krb5.conf file to specify the KDC/AD machine details for the weblogic server connectivity. This file will be present under /etc/krb5.conf, copy this file and edit it as per the requirement mentioned below.
weblogic_domain = /apps/oracle/product/middleware/user_projects/domains/weblogic_domain/
Copy the keytab files generated in step III above to your weblogic sso_domain.
As we have four keytab files we need to merge these files into one, In order to do this please follow below steps.
Ktutil
Ktutil: rkt Node1.HTTP.keytab
Ktutil: rkt Node2.HTTP.keytab
Ktutil: rkt fusiontest.HTTP.keytab
Ktutil: rkt kerberosadm.HTTP.keytab
Ktutil : wkt sso_all.keytab
Ktutil : q
Note : Source the /usr/kerberos/sbin for ktutil command.
Run the following command to test the keytab and generate a cache for the kerberos ticket:
kinit -V -k -t /apps/oracle/product/middleware/user_projects/domains/weblogic_domain/sso_all.keytab HTTP/kerberosadm.domain.com.au@DOMAINABC.COM
The output should be “ Authenticated to Kerberos v5”.
klist command at $ prompt should have the details of the cahced ticket.
So, by now your domain root folder sso_domain should have 3 files,
create a file by name “setSSODomainEnv.sh” with below details in it.
Note : Contents here are references from one of the oracle sites. Please use them for referential purposes only.
Happy Reading/Happy sharing.
Errors/Solutions
kinit(v5): Cannot find KDC for requested realm while getting initial credentials
Soln:setting the environment variable KRB5_CONFIG=<absolute path of the krb5.conf file> fixes this issue
kinit(v5): Cannot contact any KDC for realm <DOMIAN NAME> while getting initial credentials.
I had assumed that since I was just working through the local host it wouldn't need it, but it turns out you need to associate a real network address with the realm name and to make sure those ports are available. so in /etc/hosts, I had to have this line:
<ip address> example.com
Solution 2:
Check the firewall settings for getting the tickets from KDC.
Setting up WINDOWS7 for DES kerberos authentication:
WINDOWS-7, by default does not support the DES(Data Encryption standards) encryption as that's older than AES(Advanced Encryption standards).
So please carry out the following configuration options at the WINDOWS-7 client machine in order for the kerberos authentication to work.
I would update with some more relevant error messages and solution that we encountered during implementation,
to be continued....
This method of enabling SSO using the Microsoft active directory - Key Distribution center has the following configuration steps. Suggest a detailed analysis of every step marked below before executing them on to your servers.
Summary of Configuration tasks.
· Collect Environment details for
- KDC/AD Machine
- Windows client
- Weblogic Server
· Active Directory Setup.
· Setting up keytab files.
· Configuration setup steps to access MS-AD and to check the key tab files.
· Configure Weblogic server to access KDC.
· Create and Identity asserter.
· Enable SSO for UCM.
· Enable SSO for Web Center spaces.
· Setups in OHS server.
· Set up the client IE browser settings.
· Test the SSO after deploying the required applications.
Environment Details.a. KDC/AD machine
OS: Windows 2003 Server
Domain: DOMAIN.COM
OS: Windows 2003 Server
Domain: DOMAIN.COM
Machine: win2003 R2.
b. Windows Client
OS: Windows XP SP3
Domain: DOMAIN.COM
Machine: win-xp
Client: IE 8
b. Windows Client
OS: Windows XP SP3
Domain: DOMAIN.COM
Machine: win-xp
Client: IE 8
c. Weblogic Server 10.3.5.0
OS: Oracle Enterprise Linux 5 64 bit.
Machine: node1 and node2
Active Directory Setup.
Create an user in Active Directory with below details.
User Name : kerberosadm(Name this user anything that suits your situation)
Pw : Password1 ( An example to reiterate the same password is referenced in later sections during password reset)

Please do not select any other option than to keep the option "use DES encryption types for this account" checked.
Node1 :
ktpass -princ HTTP/node1.domain.com.au@DOMAINABC.COM -pass Password1 -mapuser kerberosadm -pType KRB5_NT_PRINCIPAL -crypto DES-CBC-CRC -kvno 0 -out node1.HTTP.keytab
Node2:
ktpass -princ HTTP/node2.domain.com.au@DOMAINABC.COM -pass Password1 -mapuser kerberosadm -pType KRB5_NT_PRINCIPAL -crypto DES-CBC-CRC -kvno 0 -out node2.HTTP.keytab
URL:
ktpass -princ HTTP/fusiontest.domain.com.au@DOMAINABC.COM -pass Password1 -mapuser kerberosadm -pType KRB5_NT_PRINCIPAL -crypto DES-CBC-CRC -kvno 0 -out fusiontest.HTTP.keytab
AD User:
ktpass -princ HTTP/kerberosadm.domain.com.au@DOMAINABC.COM -pass Password1 -mapuser kerberosadm -pType KRB5_NT_PRINCIPAL -crypto DES-CBC-CRC -kvno 0 -out kerberosadm.HTTP.keytab
Note: Here I'm configuring SSO for 2 node weblogic cluster and F5 load balancer. So the steps may slightly alter depending on your configuration.
è Now there would be four keytab files under the root directory of the user logged into the command prompt.
“C:\Documents and Settings\redrockadm”
1. Node1.HTTP.keytab
2. Node2.HTTP.keytab
3. fusiontest.HTTP.keytab
4. kerberosadm.HTTP.keytab
Note: This is a very important step, please make sure that the user kerberosadm has four SPNs set, this can be confirmd with the command “setspn –L kerberosadm”
Copy/FTP all the four key tab files to Node1 of the weblogic server machine.
Create krb5.conf file to specify the KDC/AD machine details for the weblogic server connectivity. This file will be present under /etc/krb5.conf, copy this file and edit it as per the requirement mentioned below.
weblogic_domain = /apps/oracle/product/middleware/user_projects/domains/weblogic_domain/
[logging] default = FILE:/apps/oracle/product/middleware/user_projects/domains/web_domain/kerb_logs/krb5libs.log kdc = FILE:/apps/oracle/product/middleware/user_projects/domains/web_domain/kerb_logs/krb5kdc.log admin_server = FILE:/apps/oracle/product/middleware/user_projects/domains/web_domain/kerb_logs/kadmind.log [libdefaults] default_realm = DIOMAINABC.LOCAL default_tkt_enctypes = des-cbc-crc default_tgs_enctypes = des-cbc-crc ticket_lifetime = 600 forwardable = yes [realms] DOMAINABC.COM = { kdc = <AD-server-ip> admin_server = <AD-server-Machine> default_domain = DOMAINABC.COM } [domain_realm] .domainabc.local = DOMAINABC.COM .domainabc.au = DOMAINABC.COM domainabc = DOMAINABC.COM [appdefaults] autologin = true forward = true encrypt = true forwardable = true |
Copy the keytab files generated in step III above to your weblogic sso_domain.
As we have four keytab files we need to merge these files into one, In order to do this please follow below steps.
Ktutil
Ktutil: rkt Node1.HTTP.keytab
Ktutil: rkt Node2.HTTP.keytab
Ktutil: rkt fusiontest.HTTP.keytab
Ktutil: rkt kerberosadm.HTTP.keytab
Ktutil : wkt sso_all.keytab
Ktutil : q
Note : Source the /usr/kerberos/sbin for ktutil command.
Run the following command to test the keytab and generate a cache for the kerberos ticket:
kinit -V -k -t /apps/oracle/product/middleware/user_projects/domains/weblogic_domain/sso_all.keytab HTTP/kerberosadm.domain.com.au@DOMAINABC.COM
The output should be “ Authenticated to Kerberos v5”.
klist command at $ prompt should have the details of the cahced ticket.
This confirms that the handshake between Linux box and the Microsoft AD/KDC is successful.
Create JAAS.login file as below to specify the login modules.
com.sun.security.jgss.krb5.initiate { com.sun.security.auth.module.Krb5LoginModule required principal="HTTP/domain.com.au@DOMAINDEV.LOCAL" keyTab=sso_all.keytab useKeyTab=true storeKey=true debug=true; }; com.sun.security.jgss.krb5.accept { com.sun.security.auth.module.Krb5LoginModule required principal="HTTP/domain.com.au@DOMAINDEV.LOCAL" keyTab=sso_all.keytab useKeyTab=true storeKey=true debug=true; }; |
So, by now your domain root folder sso_domain should have 3 files,
1. JAAS.login.
2. Krb5.conf
3. *.sso_all.keytab files.
create a file by name “setSSODomainEnv.sh” with below details in it.
## # Environment file for SSO Configuration. ## export KRB5_CONFIG=${DOMAIN_HOME}/krb5.conf JAVA_OPTIONS="${JAVA_OPTIONS} -Dsun.security.krb5.debug=true -Dweblogic.security.enableNegotiate=true -Djavax.security.auth.useSubjectCredsOnly=false -Djava.security.auth.login.config=${DOMAIN_HOME}/jaas.login -Djava.security.krb5.conf=${KRB5_CONFIG} -Djava.security.krb5.realm=DOMAINDEV.LOCAL -Djava.security.krb5.kdc=135.101.82.36:88 -Djava.security.debug=configfile,configparser,gssloginconfig" export JAVA_OPTIONS -where ${JAVA_OPTIONS} are referenced from previous settings in weblogic server + setting above; ${DOMAIN_HOME} - : /apps/oracle/product/middleware/user_projects/domains/web_domain ${KRB5_CONFIG} : Set above to ${DOMAIN_NAME}/krb5.conf file |
Note: Here we are setting up the environment for Single Sign On in weblogic server.
Reference the above file from “setDomainEnv.sh”, which in turn will be referenced by startweblogic.sh Restart the entire domain and all the managed servers involved.
a. Start weblogic server console and create an identity asserter with the navigation as provided below.
1. Login to weblogic admin console.
2. Click “Security Realms”
3. Click “My realms”
4. Click “Providers”
5. Click “Authentication subtab”.
6. Click New to create a new “ Identity Asserter” and Reorder using the button provided so that the Newly created Identity asserter is the first in the order as provided in the above screen.
7. Click on the authentication provider you just created from the list of providers.
8. Open the configuration tab and Provider Specific tab and check “Forms Based Negotiation Enabled” .
Deploy an application to the weblogic server, This will be useful in testing the application for SSO.
Deploy a test application to weblogic server similar to “Sample SSO application” under the note : 779272.1
Note: we are currently deploying only two applications 1. UCM and 2. Inbound refinery (IBR).
- Log in to the Oracle WebLogic Server Administration Console.
- Click Deployments in the Domain Structure navigation tree.
- On the Control tab, click Next until you see the Oracle UCM deployment you want to change:
- Oracle Universal Content Management - Content Server
- Oracle Universal Content Management - Inbound Refinery
- Select the checkbox to the left of the deployment to be changed.
- Click Update.
- Under the Deployment plan path, select Change Path.
- Navigate to and select the appropriate plan file:
- cs-deployment-plan.xml (for Content Server)
- ibr-deployment-plan.xml (for Inbound Refinery)
- Verify that Redeploy this application using the following deployment files is selected.
- Click Next.
- Click Finish.
Use the application “cs-deployment-plan.xml” after FTPing it onto the server.
<?xml version='1.0' encoding='UTF-8'?> <deployment-plan xmlns="http://xmlns.oracle.com/weblogic/deployment-plan" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation= "http://xmlns.oracle.com/weblogic/deployment-plan http://xmlns.oracle.com/weblogic/deployment-plan/1.0/deployment-plan.xsd" global-variables="false"> <application-name>ibr.ear</application-name> <variable-definition> <variable> <name>http-only</name> <value>false</value> </variable> </variable-definition> <module-override> <module-name>ibr.war</module-name> <module-type>war</module-type> <module-descriptor external="false"> <root-element>weblogic-web-app</root-element> <uri>WEB-INF/weblogic.xml</uri> <variable-assignment> <name>http-only</name> <xpath>/weblogic-web-app/session-descriptor/cookie-http-only</xpath> </variable-assignment> </module-descriptor> </module-override> </deployment-plan> |
Enable SSO for Web Centre Spaces.
Once you have completed the steps for configuring the Negotiate Identity Assertion Provider and Active Directory Authenticator, and all applications on your WebLogic domain are configured for single sign-on with Microsoft clients in the required domain, a final step is required to provide a seamless single-sign-on experience for your users when accessing WebCenter Spaces. There are two options for doing this: •Turn off public access, by logging in to WebCenter Spaces as an administrator and removing View access from the Public-User role. When public access is turned off, accessing the URL http://host:port/webcenter takes the user directly to the authenticated view rather than the default public page which has a login section. This is recommended when users are accessing WebCenter Spaces only using Internet Explorer, and are confined to the domain where WNA is set up. •If you must retain public access to WebCenter Spaces, then the recommendation is to use the oracle.webcenter.osso.enabled flag when starting the WLS_Spaces server. This flag tells WebCenter Spaces that SSO is being used and no login form should be displayed on the default landing page. A Login link is displayed instead that the user can click to invoke the SSO authentication where the user will be automatically logged in. If Firefox is used to access WebCenter Spaces within the Windows network configured for WNA, or any browser is used to access WebCenter Spaces from outside the Windows network domain, users see the login page after clicking the Login link. |
Note : Contents here are references from one of the oracle sites. Please use them for referential purposes only.
Local Intranet Domains.
In the local intranet popup, ensure that the “Include all sites that bypass the proxy server" and "Include all local (intranet) sites not listed in other zones" options are checked.
In the local intranet(Advanced) dialog box, add all the relative domain names that will be used for weblogic server instances participating in the SSO configuration ex: myhost.example.com and click OK. |
Configure Intranet Authentication
|
Verify the Proxy Settings.(Only if the proxy server is enabled).
exceptions
|
Set Integrated Authentication for Internet Explorer.
|
Please log in and test your SSO using any of the deployed applications.
References:
http://docs.oracle.com/cd/E24329_01/web.1211/e24422/sso.htm#i1106670
http://technet.microsoft.com/en-us/library/cc780469(WS.10).aspx
Please let me know if we can any way improve the contents of this blog, I'll be more than willing, with a comment referring you name on it.Happy Reading/Happy sharing.
Errors/Solutions
kinit(v5): Cannot find KDC for requested realm while getting initial credentials
Soln:setting the environment variable KRB5_CONFIG=<absolute path of the krb5.conf file> fixes this issue
kinit(v5): Cannot contact any KDC for realm <DOMIAN NAME> while getting initial credentials.
I had assumed that since I was just working through the local host it wouldn't need it, but it turns out you need to associate a real network address with the realm name and to make sure those ports are available. so in /etc/hosts, I had to have this line:
<ip address> example.com
Solution 2:
Check the firewall settings for getting the tickets from KDC.
Solution 3: In my case the issue was resolved by choosing port :88.
Setting up WINDOWS7 for DES kerberos authentication:
WINDOWS-7, by default does not support the DES(Data Encryption standards) encryption as that's older than AES(Advanced Encryption standards).
So please carry out the following configuration options at the WINDOWS-7 client machine in order for the kerberos authentication to work.
Go to Local Security Policies(By typing “Local Security Policies” in run dialog)->Local Policies->Security Options->Network security: Configure encryption types allowed for Kerberos:
Here select checkboxes against DES_CBC_CRC, DES_CBC_MD5 and RC4_HMAC_MD5.
I would update with some more relevant error messages and solution that we encountered during implementation,
to be continued....



Rajiv, great article. Having followed the documentation and your blog article, everything seems to be setup correctly in an environment but is still not working. AES-256 tickets appear to be being issued even though the user is defined in AD to use DES encryption and Weblogic cannot decrypt them. The AD is running 2008R2 but DES has been enabled on it. Any idea what might be causing it? Any way we can contact you directly regarding this?
ReplyDeleteHi Richard,
ReplyDeleteThanks and glad that its of help to you. when user tries to login to the application, whats the error that its throwing? based on the error I will be able to provide more inputs.
-Rajiv.
Richard,
ReplyDeleteWhat is Client Operating System?
In Windows 7 and Windows Server 2008 R2, you must configure your computers to use the DES-CBC-MD5 or DES-CBC-CRC cipher suites. If your environment requires DES, then this setting might affect compatibility with client computers or services and applications in your environment.
The Configure encryption types allowed for Kerberos policy setting is located in Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options. To load the “Local Group Policy Editor”, type gpedit.msc in run prompt.
Thanks,
Paz Periasamy
Thanks for your tutorial. I wanna implement SSO in WebLogic Server, how can I perform?. I am completely new one in this field. Any suggestions are welcome.
ReplyDeleteAlong with the steps outlined in this blog, please check on the version of the windows operating system where the key tab files are being generated from.
ReplyDeletebefore testing, make sure to check all the browser/weblogic settings
thoroughly, minor setup issues would lead to recheck/redo all your configurations.
Good Luck!
I have a webapp deployed in WL that is doing this. Everything is working fine when I access a webpage from this webapp. I recently made a change to the webapp to invoke a webservice (restful) that is running on the same WL server. I noticed that the webapp is not sending required identity information to the webservice and it is failing with authentication error. Do you have any inputs on why this could happen and confirm if the identity provider is actually stripping of security info after authentication?
ReplyDelete